In this first of two installments of “A Seismic Shift in the Digital Health Landscape” we analyze the significance of the recent theft and disclosure of NSA-developed malware, and what it means for developers looking forward.
Developers, do you feel it? A seismic shift in the digital landscape is rumbling right now, and securing data just got more difficult. The fault zone? Global. The cause? The widespread release on April 08, 2017 of over 1,000 malware files stolen somehow from the US National Security Agency (NSA). That’s right, malware developed by the nation’s top spy agency, including many zero-day exploits, is now in wide, uncontrolled circulation. And many more exploits are being released over time by threat actors known only by such names as The Shadow Brokers and The Equation Group.
Behind the WannaCry Ransomware Worm
The ransomware worm known as WannaCry, currently the largest such outbreak in digital history, included at least one of the stolen NSA exploits, code-named ETERNALBLUE. But the NSA malware unlocked on April 8th has the potential to complicate data and network security for a long time to come, especially for users of Microsoft Windows systems. According to tracking firm Net Market Share, more than 65 percent of desktop computers worldwide are running vulnerable Windows software, which includes all Windows software up to Windows 10. What’s worse, one of the NSA exploits, known as FUZZBUNCH, is specifically designed to thoroughly compromise Microsoft Windows Server 2008, the most widely used server software of its type.
Other exploits recently released include tools to compromise various brands of firewalls, routers, and security appliances from many vendors. Also available, apparently, are many anti forensic tools designed to make detection difficult and attribution near impossible. The advanced methods in such malware allow for encrypted storage of files and data exclusively in a system’s registry, often for later exfiltration. Other modules are capable of reprogramming hard disk firmware to provide a truly undetectable, persistent threat, as well as the ability to create and access hidden sectors on drives for data storage and later exfiltration. [Link, see page 31]
Health Data is Especially Valuable to Data Thieves
In the face of this unprecedented threat, a key challenge for health app developers is that health data is a more valuable commodity than financial data in darkweb marketplaces, making health data a more attractive target for cyber criminals. Health data contains a wealth of information that can be used for fraud and identity theft, such as social security numbers, addresses and claims data. While a credit card record might fetch $2 on the black market, a medical record can average more than $20. Health data is also more valuable, and more targeted, because identity theft is harder to detect and mitigate in healthcare. Credit cards can be canceled and replaced in a few days, but there is no corresponding remediation for health records, once they’ve been breached.
Cybercrimes Invoke HIPAA Duties
Health app developers should know that whenever US health data is involved, HIPAA is implicated. When ransomware or other cyber crimes occur, HIPAA duties are automatically invoked. First, the OCR (HIPAA’s enforcement agency) presumes a breach in the case of a ransomware attack, unless the data was encrypted to current NIST standards or better. An affected entity must determine whether such a breach is a reportable breach no later than 60 days after the entity knew or should have known of the breach. A request by law enforcement to delay breach reporting however, can extend the 60-day reporting deadline.
Next, developers must understand that reporting ransomware incidents, cyber crimes, or providing breach information to law enforcement, DHS, or CERT does not satisfy HIPAA’s requirement to report breaches to the OCR, and sometimes, directly to the media. HIPAA-required reports of health data breaches must still be made to the OCR, as required by HIPAA’s Breach Notification Rule. To avoid breach notification after a ransomware incident, a breached entity would need to prove, through forensic or other evidence, that the data was encrypted to NIST standards when the attack occurred, and the ransomware merely re-encrypted already-encrypted health data.
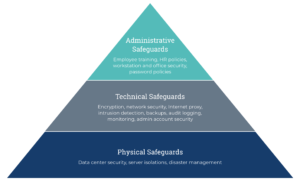
Finally, it’s critical for health app developers to understand that full compliance with HIPAA actually helps protect against cybercrime, and makes recovering from malware incidents faster and easier. This is because HIPAA compliance require plans to be in place (and tested periodically) for emergency operations, access authorizations, termination of access when no longer appropriate, protection from malware, proper password management, login monitoring, data backups, disaster recovery, and appropriate encryption procedures, to name a few. Far from being a burden, HIPAA is surprisingly beneficial for developers. It helps ensure that appropriate data and privacy protections are in place and are maintained over time.
Customary IT Security Isn’t Good Enough Any More
The wide disclosures of NSA hacking tools this year have opened a new salvo in the battle to keep data and systems secure. Too many surveys show that commonly accepted IT safeguards are not being broadly implemented, and IT best practices are still out of reach for many organizations. Whether from budgetary constraints, lack of cybersecurity talent, or leadership apathy, such failings simply aren’t good enough anymore. Like it or not, market forces and hackers are creating a more severe business operating environment. Digital “survival of the fittest” is becoming the norm. Highly secure organizations will endure. Security laggards will not.
See Part 2 for important suggestions for developers on how to rise above this unprecedented threat.