
HIPAA Enforcement Is Serious Business
Developers beware. After years of inaction, HIPAA enforcement has awakened with a vengeance. The Office for Civil Rights (OCR), HIPAA’s official enforcement agency, levied fines against HIPAA-regulated entities in 2016 alone totaling $22,855,300. Seven of those so-called “settlements” exceeded $1,500,000. The largest settlement in 2016 was against Advocate Health Care Network for $5.5 million. In 2017 so far, the OCR has fined Presence Health $475,000 solely for delayed breach notification.
The OCR Is Not the Only HIPAA Enforcer Now
The OCR, officially responsible for HIPAA enforcement nationwide, is not the only HIPAA enforcer anymore. Changes to HIPAA from the HITECH Act, effective in 2010, gave all fifty State Attorneys General (SAGs) the power to bring HIPAA-based civil suits in federal courts on behalf of their State’s residents. And SAGS are beginning to act under these new powers. On June 15, 2017, New York’s Attorney General announced a fine of $130,000 for a NY-based company that provides healthcare-related IT services. The penalty was for delaying the reporting (by more than one year) of a data breach that compromised 220,000 patient records of New York residents.
In addition to the OCR and the SAGs, another entity has begun to enforce HIPAA-related violations: the Federal Trade Commission (FTC). Though it has no legal authority to prosecute HIPAA violations directly, the FTC has been executing enforcement actions that take a parallel legal track, by investigating the business practices of entities regulated by HIPAA. In 2014, a federal court upheld the FTC’s power to sue companies that fail to protect customer data. And the FTC has sued dozens of companies in recent years for data protection failures.
For developers bringing apps to market that are considered “medical devices”, the US Food & Drug Administration (FDA) is another entity that can bring severe penalties and enforcement actions. Clearly, developers must do everything they can to avoid attracting the attention of enforcement agencies. To avoid enforcement however, developers need a deeper understanding of enforcement processes, along with an understanding of what constitutes a violation under HIPAA.
HIPAA Violations Vary in Severity
The OCR operates under the current HIPAA Regulations (Regs), which stipulates that certain categories or types of violations are more serious than others. The seriousness of HIPAA violations is determined in part by the degree of (or lack of) “willfulness” of the violator, as well as whether the violator took timely steps to correct the violation.
When a violation is determined to have occurred, the OCR has identified five factors it typically considers in determining the amount of a civil money penalty:
- The nature and extent of any violation, including number of individuals affected and the duration of the violation.
- The nature and extent of victims’ physical, financial, or reputational harm, including any hindrance to victims’ ability to obtain health care.
- The history of prior noncompliance, including similar prior indications of noncompliance and the offending party’s responses to them.
- The financial condition of the offending party, including difficulties that could have affected compliance or that could cause a money penalty to jeopardize the future provision of health care.
- Such other matters as justice may require, a catch-all category of potential issues.
Severity Categories and Civil Monetary Penalties for HIPAA Violations
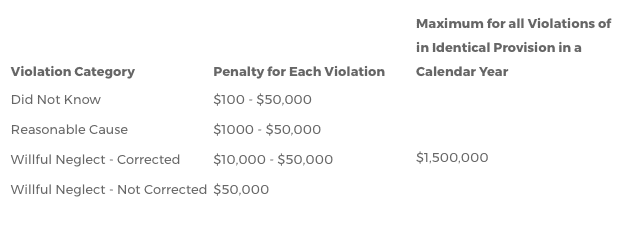
Potential Civil Penalties from the OCR:
- $100 to $50,000 or more per violation
- Up to $1.5 million per calendar year for all violations of an identical provision
- Limits are per type of violation (e.g., four types of continuous violations over three years can equal $18 million!)
Potential Civil Penalties from State Attorneys General (SAGs):
- Up to $100 per violation
- Up to $25,000 per calendar year for all violations of an identical provision
- Attorneys’ fees
- Likely to combine with additional charges under state law
- SAGs might not adhere to HHS enforcement guidance, and are not required to.
Developers, Beware of “Willful Neglect” Violations
HIPAA Regs today define “willful neglect” as: “conscious, intentional failure or reckless indifference to the obligation to comply” with HIPAA. Since the HITECH Act, the OCR is now required to formally investigate every complaint where a preliminary investigation indicates a possible (as opposed to probable) violation due to willful neglect. Developers who mistakenly believe that HIPAA compliance is only for the app and not for the developer or business, and who act accordingly, may be prosecuted by the OCR for willful neglect. If a failure to comply is determined to be “willful neglect” and was “not corrected”, the OCR can charge the developer under the most severe category shown in the chart above.
What Can Trigger Enforcement’s Attention?
Developers must do all they can to avoid attracting the attention of enforcement agencies. Any number of things can put a developer on enforcement’s radar, such as:
- Complaints to the OCR or other agencies from employees, patients, whistleblowers, board members or the public. Any person can file a HIPAA compliant, and there is no cost to do so.
- Media reports of violations or questionable privacy/security practices.
- False claims about the degree of privacy, security, or usefulness of an app or product for specified purposes.
- Failure to perform an adequate, HIPAA-required Risk Analysis.
- Failure to report data breaches in a timely manner and/or to the appropriate authorities.
- Routine OCR audits or compliance reviews.
Best Tactics to Stay Off of Enforcement’s Radar
The following tactics will help developers minimize the chances of being singled out for investigation or prosecution for HIPAA violations:
- Become and remain fully compliant with HIPAA.
- Perform a gap analysis to determine what compliance requirements may have been missed in the compliance process.
- Make sure an updated Risk Analysis is conducted, and the Analysis accurately reflects vulnerabilities addressed in HHS guidance, such as mobile devices, ransomware, etc.
- Revise privacy and security policies and procedures to bring the organization into full compliance. Fine-tune existing data-protection policies and procedures based on guidance and experience.
- Revise breach notification policies, procedures, and breach response plans, particularly with respect to conducting a breach-related risk assessment for determining whether notification is required or not.
- Train and retrain yourself and your workforce, and promote more ongoing awareness of health data privacy and security.
- Revisit all BA Agreements and ensure they accurately reflect real business processes as well as HIPAA’s requirements and data disclosure limitations.
- Determine whether any forms, such as requests for access, should be created or updated.
- Take advantage of HIPAA’s Safe Harbor Provision and encrypt all PHI according to HHS guidance. This includes data at rest and data in motion.
Developers, along with becoming fully HIPAA compliant, the best general strategy to avoid HIPAA enforcement is to protect HIPAA-regulated data with strong encryption. It’s far less costly — in dollars and reputation — to prevent HIPAA problems in the first place than to clean up the damages from a data breach, negative publicity, or enforcement actions.
Was this article helpful? Subscribe below to learn more about MedStack and get tips delivered straight to your inbox.




